These are the values that you would like to retrieve after the stack operations have been completed. You can access them via the console or CLI commands, or reference them in other templates as imports. This approach ensures that the templates are of a manageable size as you don’t have to put allthe resources together in one big file. You can define an output value using the Outputs construct:
Outputs:
InstanceID:
Description: ID of the EC2 instance
Value: !Ref EC2Instance
As soon as the stack operations are complete, you can access the identifier of the new EC2 instance using the InstanceID key.
The concepts we’ve covered so far should help you get started with the practical day-to-day usage of the CloudFormation service. To make debugging issues easier, let’s discuss the internals of how CloudFormation works under the hood.
How CloudFormation works
AWS services such as CloudFormation are great at reducing the cognitive load of the end user. A lot of internal details are abstracted, exposing only the functionalities that the users need. However, in certain situations, it’s important to understand what the service is internally doing. This not only helps debug problems faster but also gives you a good thinking ground when discussing topics such as security, compliance, and day-to-day operations for your organization.
Permissions delegation for resource management
By default, AWS CloudFormation uses the permissions of the user that invokes the CLI commands or uses the service directly in the web console. So, in a way, the end user delegates authority to the service for temporary use. If you face any permission denial issues, then this is the first thing you should be checking.
For all stack operations, CloudFormation generates temporary security tokens that match the user’s IAM permissions. This sequence of actions is highlighted inFigure 4.1. Using this token, the service invokes the API endpoints of all services you are creating resources for. For example, if you are creating an EC2 instance in the eu-central-1 region, CloudFormation will use the regional EC2 service endpoint, ec2.eu-central-1.amazonaws.com, and register an instance creation request on your behalf. If required, you can also define a service role in IAM. This role can then be assumed by the service during any stack operation. You can leverage this to scope different permission sets for the service than what the user possesses. This service role needs to be passed as an argument when the stack is first deployed:
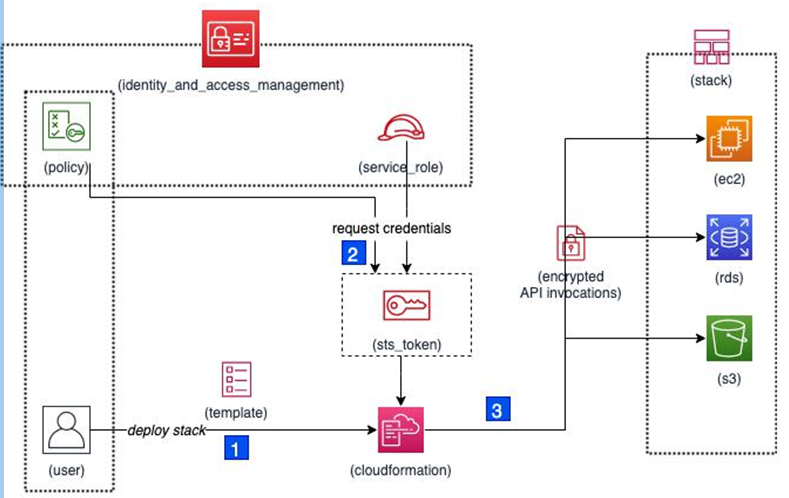
Figure 4.1: Sequence of operations when working with CloudFormation